April AI is an innovative tool designed to enhance communication and leadership skills seamlessly, without adding extra learning hours to your schedule. Engineered to seamlessly integrate into your existing routines, April AI makes learning effortless.
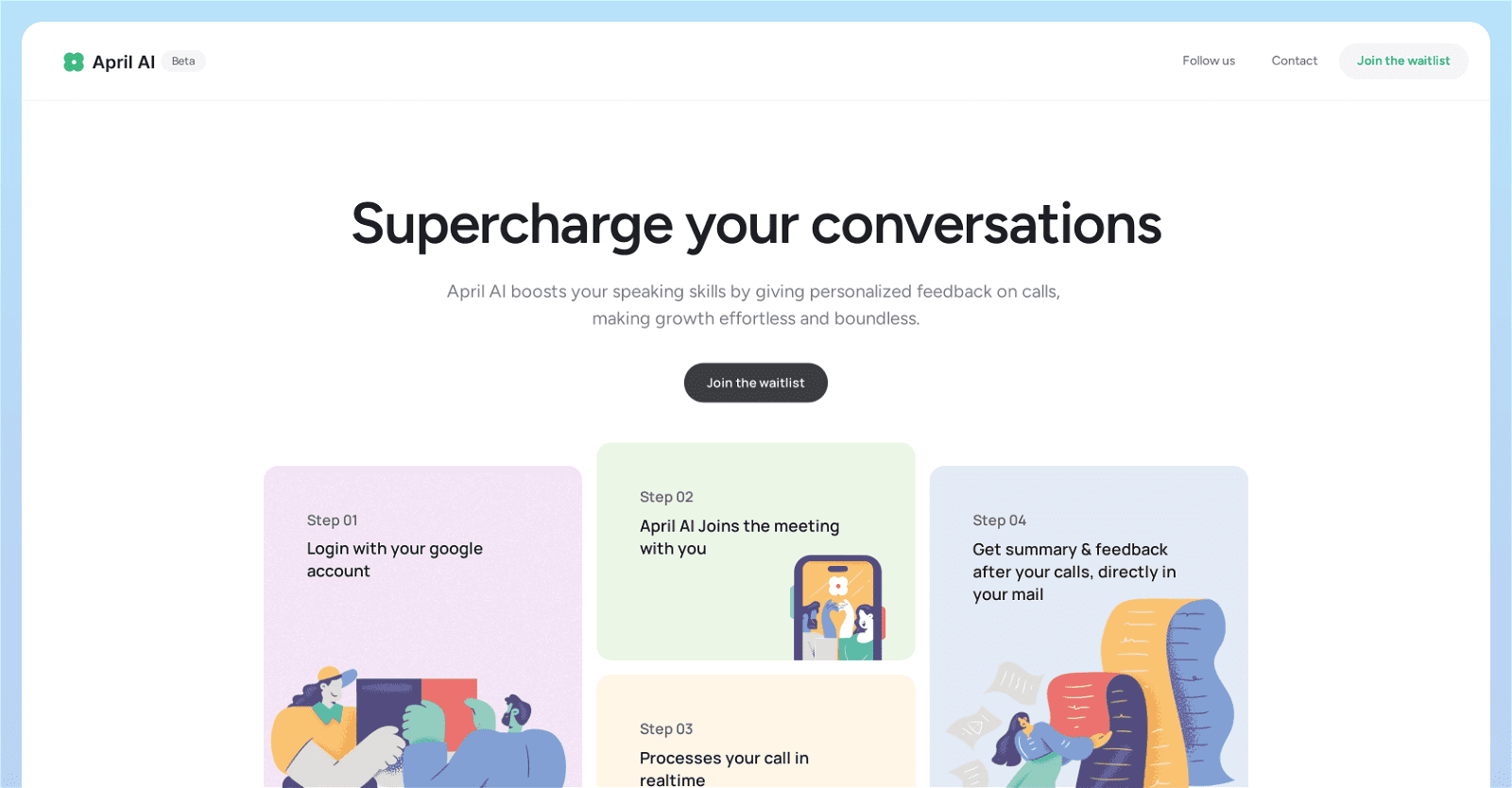
Its core function focuses on improving speaking skills by offering contextual and personalized feedback during calls. By logging in with your Google account, April AI joins your meetings, analyzing conversations in real-time.
Post-meeting, users receive a concise summary and personalized feedback via email. April AI’s understanding of the subtleties of real-life meetings ensures that advice aligns with each user’s unique style.
This personalized approach means that individual growth paths are tailored specifically to each user. April AI is crafted with busy professionals in mind, seamlessly integrating into existing workflows without requiring additional time for learning.
More details about AprilAI
What does ‘contextual feedback’ from April AI entail?
‘Contextual feedback’ from April AI means that the feedback provided takes into consideration the specific circumstances or setting of the meeting. It goes beyond simply analyzing what was said, understanding the nuances of the conversation to offer personalized advice that aligns with the context.
How does April AI contribute to improving speaking skills?
April AI enhances speaking skills by analyzing conversations during calls in real-time and delivering personalized feedback. By considering the context of the meeting and your individual speaking style, the feedback provided is highly relevant and effective for your skill development.
How does April AI integrate with my Google account?
To utilize April AI, users log in with their Google account credentials. Once logged in, April AI seamlessly joins meetings, where it tracks and analyzes conversations in real-time to provide valuable feedback.
What measures does April AI take to ensure privacy and data security?
April AI’s approach to privacy and data security is detailed in its Privacy Policy. While specific details may vary, typical measures include encryption protocols, access controls, and adherence to data protection regulations to safeguard user information.